In its latest round of Spring Cleanup Google has waved a red flag on quite a few of its services including Google Reader – the RSS reader service which was launched back in 2005.
Tech Guide
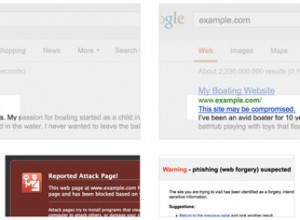
Google launches Help for Hacked Sites Series with articles and videos
With the passage of time, DDoS attacks and hacking attempts have increased a lot and many people are falling victim to this act and losing their site and valuable data to hackers.
What Are TED Conferences: Your Ultimate Guide
Have you ever had an issue or subject you are extremely passionate about, or a thought you wanted to share but didn’t have a venue to share it. The TED conference is that venue for influential individuals, movers, and shakers in a certain subject.
How to Survive Working in an Office
In Silicon Valley, the technology hub of the United States, being able to work from home is a luxury not all companies offer.
How to Select a Proper Touchscreen Monitor
Touch panel technology took root in our daily lives. It made a huge impact on every sphere of our existence, from digital gadgets like smartphones, gaming consoles, and tablets to many more like bank ATMs, ticket machines in airports or train stations, electronic kiosks in malls, and even navigation displays in modern cars.
Windows 8: Everything about the Logged in User Account
The general public may be a bit lost in launching Windows 8 for the first time. Not so with the new interface (formerly Metro) that serves the “Start” menu (even if it failed a bit at first). But because with the new Microsoft operating system, the “Cloud” is becoming a reality more than concrete.