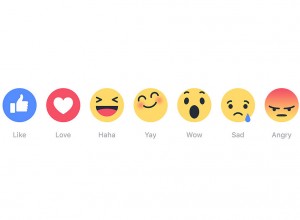
If you have recently logged in to your Facebook account, you might have noticed a suite of new buttons in addition to Like that displays a variety of reactions or, more suitably, emotions. This might have come as a disappointment to many Facebook users who have anticipated a Dislike button instead.
News
Will Amazon’s cloud service succeed with major US banks?
Amazon is looking to the giant banking firms in the United States in a move to expand its cloud computing market by trying to convince such companies as J.P. Morgan, Goldman Sachs and Citigroup of great savings when they opt to pick Amazon’s servers for high-performance computing tasks rather than build their own storage platforms.
As Twitter grows, does it even take your security seriously?
The answer could be a big no, take only a look at a recent incident involving Twitter’s password recovery feature, which was struck by a bug that caused thousands of personal information such as email addresses and phone numbers to be exposed to attacks.
In India, a massive phishing campaign against the country’s largest bank
More than 13,000 ATMs. Over 4,000 bank branches. These figures only represent a large swath of victims in a massive phishing campaign that hit ICICI, the largest private bank in India.
Are tech companies against the national security of United States?
Tim Cook’s tenacious resistance to the FBI’s request for a backdoor access to the iPhone used by the San Bernardino shooter has led some to conclude that tech companies are somehow sympathizing with terrorists and criminals.
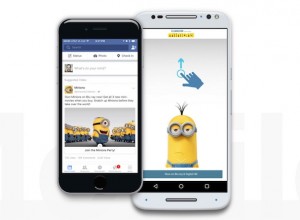
Facebook revolutionizes the way ads are delivered through Canvas
Launching ads in any format on Facebook, the popular networking site, represents a huge challenge for Mark Zuckerberg and company. For one, it could make or break the business that heavily relies on ads to keep going.