In recent years, we often had just a couple of choices when it comes to buying a game console for our living room, it is either a Playstation 4, a Xbox One or a Nintendo Wii U. And the reason I haven’t bought one since the Playstation One is because I prefer gaming on PC and I […]
Blog
An eBay Seller Shipped an Empty Box and I Lost $370, this is How to Protect Yourself and Receive Refund
If you are searching for scams against online buyers on Google, you will see results related to eBay dominate the search results. It is not by chance that most of those links lead to articles on how to avoid getting scammed by eBay.
The Era of the Smartwatch (And Why a Rugged Model is Often the Best Choice)
Over the past decade or so, we’ve seen some amazing advancements in smartphones. From their humble beginnings, they were always something of a head turner and conversation starter, and over the years, they have evolved from being a simple telephone to a device that combines a portable computer, video recorder, camera, fitness tracker and so […]
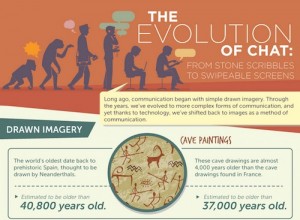
The History of Chat from Stone Scribbles
Do you remember MS-DOS? Was your first chat experience on AOL or IRC? Do you remember the click of the rotary telephone – probably the only phone in your home? Back in the day, we had to pull up a chair and sit at our computers to communicate online. If you used the old chat […]
Enterprise Resource Planning Solutions for Warehouses
Warehouses can benefit greatly from Enterprise Resource Planning (ERP) solutions. Innovative software is available for mobile devices that are used to scan products. Traditional bar code scanners are used along with other smart gadgets that have capabilities for reading different types of codes and graphics that are printed on product packages.
Increase of People Watching Others Play Online Games
The trend of gamers watching other gamers play is expected to increase in popularity in the coming years as more online streaming platforms and more conventions become available.