It’s more normal now than ever before to have a mobile phone. In fact, many people even have more than one and barely anyone leaves the house without checking they have their mobile on them. But who actually remembers where it all began?
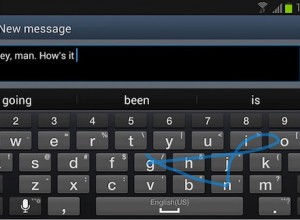
Swift keyboard on Samsung devices exposes users to remote attacks
The problem with built-in apps in mobile devices comes forth when a security hole associated with it presents a real threat to the users.
Apple Watch vs Android Wear: Which way to go?
There are a lot of differences between the Apple Watch and Android Wear operating systems for wearables. These differences are quite noticeable in that both platforms vary tremendously in design. Apple Watch is centered on mobile applications while Android Wear focuses on cloud computing.
Dell Uncovers Malware Hiding in Images
It is just natural for a malware to be hidden somewhere so that it becomes tricky and hard for would-be victims to fail to notice it. And nowhere is it more difficult to detect a malware than in images you think are safe but actually contain malicious codes.
Why you shouldn’t upgrade to Android M beta version
Google already confirmed that the next-generation Android M operating system is set for release in late 2015. The Android M is rolling out to majority of mobile devices worldwide that run the Google-developed operating system, meaning not all will have it.
Facebook is working on an AI project, should we worry?
The scenes from the 2014 film Transcendence offers some level of perspective on the devastating consequences if artificial intelligence overcomes our planet. That is why Facebook’s move to gather a team of researchers to develop artificial intelligence for the social networking giant should cause a lot of concern.