It’s more normal now than ever before to have a mobile phone. In fact, many people even have more than one and barely anyone leaves the house without checking they have their mobile on them. But who actually remembers where it all began?
Blog
Prevent Visual Hacking with 3M Privacy Filter
This is a sponsored post written by me on behalf of 3M Company for IZEA. All opinions are 100% mine. While high-tech cyber attacks become so popular these days, there is another risk of the old-fashioned physical spying in your office that you shouldn’t ignore, it is also called visual hacking.
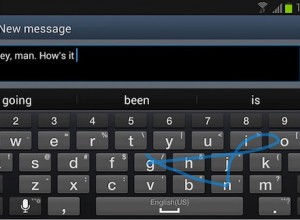
Swift keyboard on Samsung devices exposes users to remote attacks
The problem with built-in apps in mobile devices comes forth when a security hole associated with it presents a real threat to the users.
Apple Watch vs Android Wear: Which way to go?
There are a lot of differences between the Apple Watch and Android Wear operating systems for wearables. These differences are quite noticeable in that both platforms vary tremendously in design. Apple Watch is centered on mobile applications while Android Wear focuses on cloud computing.
Alienware 17 ANW17-6421SLV Gaming Laptop Review
I’ve reviewed some gaming laptops this year from ASUS and MSI. The ASUS ROG G751JY-DH72X comes with the powerful NVIDIA GeForce GTX 980M graphics processor and I was quite satisfied with its performance. Unfortunately, that laptop is not suitable for many gamers due to the high price tag of nearly $3000.
Dell Uncovers Malware Hiding in Images
It is just natural for a malware to be hidden somewhere so that it becomes tricky and hard for would-be victims to fail to notice it. And nowhere is it more difficult to detect a malware than in images you think are safe but actually contain malicious codes.