Computer technology firm Oracle Corporation has just released Critical Patch Update (CPU) for Java SE days after several exploits in its software were detected, including the one highlighted in the recent Twitter cyber attacks that left more than 250,000 accounts compromised.
Java 7 Update 10 is remarkably earlier than the original schedule on Feb. 19, as the California-based company rushed to address “active exploitation in the wild of one of the vulnerabilities affecting the Java Runtime Environment (JRE) in desktop browsers.”
However, the update can be yet another staple of security risk for unsuspecting users after researchers uncovered a new bug to the framework that could allow cybercriminals to bypass a fully patched protection framework designed to counter silent exploits. The CPU, an aggregate of patches for various security vulnerabilities, touches on 50 security issues in the software, for which Oracle urges users to immediately download the update as soon as possible. Although Oracle didn’t specify what zero-day vulnerability is being addressed by the CPU, it is clear from the eyes of security researchers why the company had cut short its timetable – Oracle hastened to fix the flawed update shipped with the previous version of Java, ironically intended to combat cyber threats to the software. The latest update lets users manually execute a Java code that doesn’t have digital certification from a trusted SSL certificate provider.
Security Explorations, a security start-up company based in Poland, said it had found a new security vulnerability in which an unsigned Java code could actually be executed on a Windows system even after performing the four Java Control Panel settings presented below:
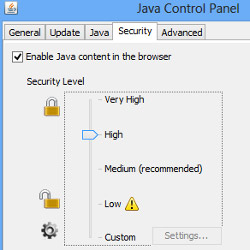
– Low
Runs unsigned Java apps in the browser even without prompting unless they request access to a specific old version of Java or to protected resources on the system
– Medium
Runs Java apps in the browser without prompting, provided that the Java version is secured
– High
User will receive a prompt on whether to run an unsigned Java app in the browser. The user may update the version if the Java version is below security baseline.
– Very High
Will not run unsigned (sandboxed) Java apps.
In a Full Disclosure, Adam Gowdiak from Security Explorations, argued that existing security measures used to configure unsigned Java applications are mere “theory”. He said that it is practically possible to run an unsigned Java code even in the absence of security settings configured in Java Control Panel.
Unfortunately, the “security improvements” brought by Oracle failed to address key security issues. To ward off security threats from this vulnerability in Java, Gowdiak advised users to use a Click to Play technology provided by a number of web browsers.
Another good practice to prevent security risks while having Java installed in your computer is to disable the applet in your browser. Turn it on only when you badly need it.



