If you are running a website that uses the Magento solution, chances are you might be the next victim of a new breed of ransomware dubbed KimcilWare, which security researchers have spotted in the wild infecting several sites.
Since the malware has just been discovered, it would be hard to establish at the moment how the attackers have managed to break into the victimized websites and encrypted the files with the use of a block cipher called Rijndael. According to initial reports, the attackers are selling the decryption key for the ransomware at $415, equivalent to one Bitcoin. Other variants of the ransomware can be decrypted at a lower cost, as low as $140.
KimcilWare was first seen as a broken Hidden Tear variant, presumably because of certain issues with the SSL connectivity of the attackers’ command and control server. The person responsible for the ransomware seems to be the same attacker behind another breach into a website infected with KimcilWare, as indicated by the ransom note, which contained the email address of the attacker.
Security researchers found some variations in the way the attacker infected the two victim sites with the ransomware, but the remarkable similarity was the email address of the attacker and the use of the Magento e-commerce platform in both websites.
Further investigation revealed that the attacker behind the KimcilWare ransomware had begun to attack the websites for more than a month now, dropping a script meant to lock out website owners by encrypting their site data. More than two types of script were used to encrypt those pieces of information, according to the researchers.
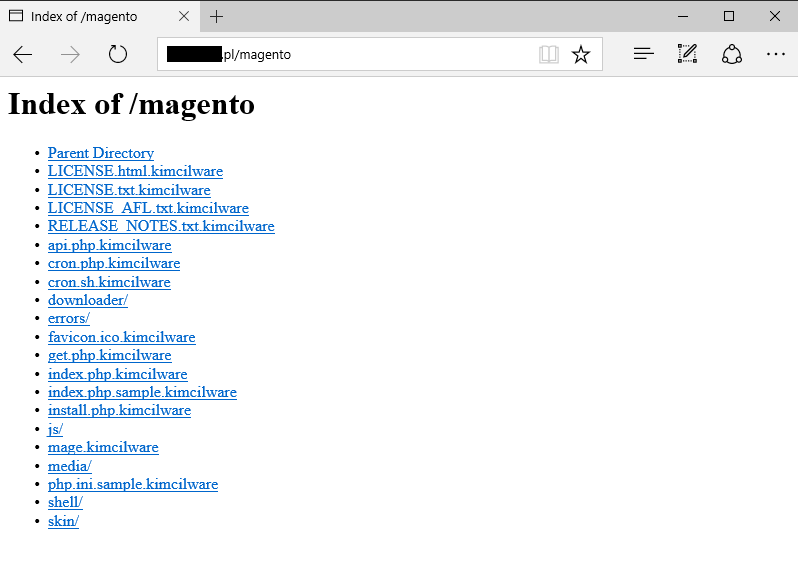
The first script will convert the files with the .kimcilware file extension to encrypt the data of the website, with the addition of an HTML file that shows the ransom note. The second script puts the .locked extension to the file that has been encrypted and displays a message containing the note for ransom, which reads that the victim must send one Bitcoin to the attacker in order to unlock the files. The Bitcoin address is included in the ransom note as well as the email address through which the victim is instructed to contact the attacker after the ransom amount has been paid.
It remains unclear how the attacker got hold of the servers being victimized, but it appears the Helios Vimeo Video Gallery extension has been exploited. Magento has yet to release a statement regarding the hacks.