Chimera, a long standing ransomware that has been targeting individuals and businesses in Germany, has recently resurfaced with a new threat to expose to the public the data it holds from its victims.
The old ransomware has been at work to encrypt computer files and network drives and ask the file’s owner for a sum to restore the stolen data. Now the creators of Chimera have elevated the features and capabilities of the ransomware to publish the encrypted pieces of information online if the owner does not give in to the demands of the attacker.
Before, Chimera used to spread via emails and links for approximately two months, according to an advisory.
There seems to be a common trend in the emails that are targeted to a specific segment of the victims. The email would contain a URL or link to a Dropbox file that the sender would claim to be containing an important information. Then the landing page would ask the target individual to download the list of files to their computer.
The risk arises when the recipient of the malicious email clicks on the download link, which will then infiltrate the victim’s computer with malware that is designed to encrypt all the data stored in the machine, as well as the network drives that are linked to the computer being attacked.
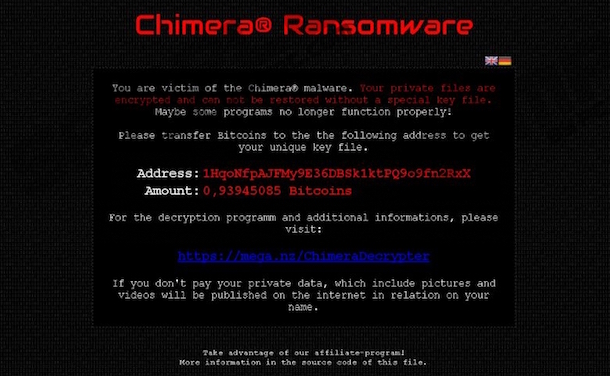
This will become noticeable as all the file extensions in your computer will be changed to .crypt, meaning your files are now encrypted and you cannot open them. What remains concealed, however, is the fact that you have just been locked out of your computer, devoid of access to your personal files, until a ransom note will greet you on your next reboot.
Chimera creators will ask their victims a ransom money of up to $685 that the victim needs to pay in Bitcoin. If you choose not to pay the ransom, the attackers will threaten you to have all of your data leaked online, although there has been no known instance of such a data leak as of this posting.
This threat is quite something new as far as the way it scares its victims is concerned. The previous version of Chimera only worked by encrypting data that had been stored in the computer’s local drive. Once the ransom was paid, the attacker would send the private encryption key to the victim to unlock the data. There was no instance also of publicly leaked data.
One way to avoid falling prey to this kind of cyber crime is to back up your data and store sensitive information in the cloud.




Peach drinkwine says
i would rather not store things into the cloud because hackers can have access to it i would much rather store it on a offsite backup and most defiantly offline