In the view of IT security firm Quarkslab, Apple lied when it said it totally couldn’t read iMessage contents. In fact, the researchers at the company said, Apple could furtively eavesdrop on conversations between users out of some sinister intentions or under government coercion.
Cyril Cattiaux, and his colleague with the handle “gg”, explained fully in a white paper the string of methods for anybody within Apple to ambush iMessages. Here’s what the presentation says in summary:
Although there is nothing yet to suggest Apple is actually reading iMessage communications, the end-to-end encryption tool used in the instant messaging system is not snoop proof, either. That means the public keys that supposedly secure the iMessage infrastructure is not hard to crack. Also, the cryptography system isn’t transparent enough to detect whether a message shows up on the device of the intended recipient or falls in the booby trap of the National Security Agency or other third-parties.
Apple’s suspicious public key server
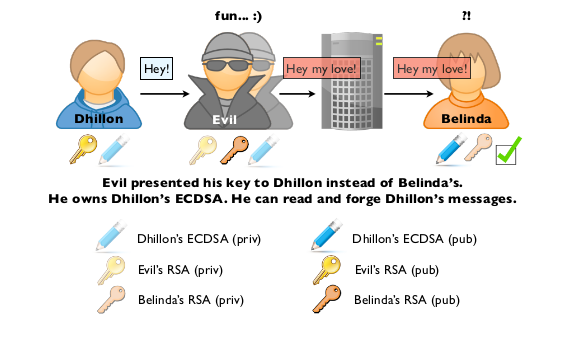
The recipient decrypts an incoming iMessage using a private key after an iOS device that extracts the receiver’s public key from Apple’s private server encrypted that message. Senders of encrypted messages need to trust the keys from Apple’s server as truly belonging to the recipient.
A server, indeed, has to be public for senders to determine any alterations to a key. Along this line, the sender is alerted whether a key can be trusted or part of a man-in-the-middle attack (when that key has been changed). But Apple of course has full control of its key server, meaning the company could decide to change the directory anytime if it wanted to read contents of iMessage.
The security flaw also extends to other Apple products such as iMac, Mac Pro, MacBook Pro, MacBook Pro Retina, iPhone, iPod Touch and iPad.
What attackers can do
What aggravates this systemic vulnerability is the capability of a hacker to stealthily change the iMessage before it turns up at the recipient’s device, without the sender and receiver knowing it.
Apple may be telling what it deems proper when it says it’s not intent on re-engineering the iMessage system to penetrate private conversations, but the flaw of the technology lingers for as long as the company refuses to address Quarkslab’s security concerns.
Apple’s recent alleged involvement in NSA’s surveillance program called PRISM remains fresh in our minds. So the tech firm’s assurance that nobody could read encrypted messages within its network is doubtful. Everyone is virtually suspect here.
Disclosure: We might earn commission from qualifying purchases. The commission help keep the rest of my content free, so thank you!



