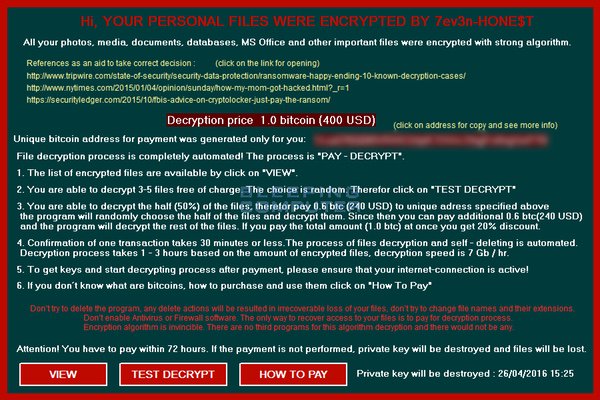
Just when you think the 7ev3n ransomware is done with you after it locked out users from their computers in January, the malware has resurfaced after months of hibernation, but with a new name and a lower fee for the decryption key.
According to security researchers at Bleeping Computer, the new variant of the 7ev3n ransomware, dubbed 7ev3n-HONE$T, has just come back into view locking users out of their documents and files and demanding 1 Bitcoin in ransom payment, equivalent to $400. Back in January, the ransomware would ask its victims to pay 13 Bitcoins (equivalent to more than $5,000), but the tactic might not have scared enough victims to pay for its hefty price.
A crypto-malware by nature, the ransomware has already targeted a great number of victims and encrypted their documents since its inception in January, converting the files with the .R5A extension and renaming them. It is also difficult for any Windows recovery tool to recoup the files because the ransomware creates a file that paralyzes all of the recovery methods in Windows computers.
But if you think that all you have to do is to pay the ransom demanded by the attackers, you might be mistaken. According to security researchers who had plenty of time observing the ransomware’s behavior, the 7ev3n ransomware continues to prolong the agony of its victims by requiring the victim to recover the deleted Windows recovery options by reinstalling the Windows disc. The victim must also wipe all the installed ransomware files from the computer and perform an antivirus scan on the infected machine.
As of now, little is known about the new variant of the 7ev3n ransomware. All that the security researchers have so far established is that the modified ransomware still employs a process of encrypting files and documents that is similar to the original version. However, the security experts could not tell how the ransomware is being spread and what, if any, malicious files are installed in a computer in the event of an attack.
Some tech pundits also assume that the source code for the original version of the ransomware has been leaked in the wild, giving other cyber crooks the opportunity to take advantage of the situation and create their own version of the ransomware, which can also explain for the cheaper ransom demand.
At any rate, the best way to avoid falling for this ransomware and other forms of attack is to ignore suspicious email attachments and to always implement software updates.
Disclosure: We might earn commission from qualifying purchases. The commission help keep the rest of my content free, so thank you!