Security experts at BleepingComputer(dot)com were quick to provide a solution to decrypt a new ransomware aptly called Jigsaw which not only encrypts your most precious computer files, but also deletes them incrementally if you do not pay the ransom.
The ZIP file for decrypting the files can be downloaded here.
This is not first kind of ransomware that threatens its victims to delete their files, but it is actually the first of its kind to carry out the treat, according to the security researchers. Perhaps it is a way employed by the attackers to fast track the processing of payment usually in Bitcoin, because most ransomware victims nowadays often resort to the help of computer experts, seeking advice as to how to best respond to the attack, which kills time before they pay the ransom demanded if all else fails.
Most of the time ransomware attackers find it difficult to identify what method works best to convince the victims to pay the ransomware as quickly as possible. But by threatening the victims that their files will be deleted in a matter of hours, the job of cashing in on the victims becomes a no-brainer.
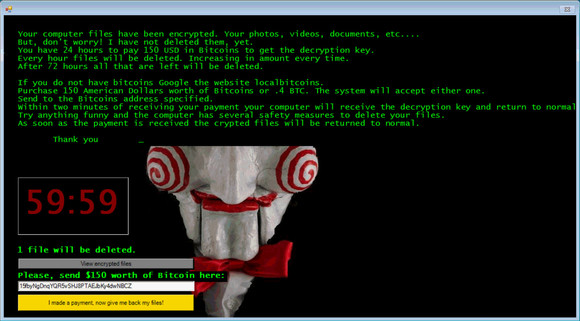
Once you are infected with the Jigsaw ransomware, you will see a ransom note on your screen asking you to pay $150 in Bitcoin in order to recover your encrypted data through a decryption key that will afterward be provided by the ransomware attacker.
You refuse to pay, and the ransomware will erase one file after the first sixty minutes. Every after an hour later 1,000 more files will be deleted until 72 hours have passed, during which all of your files will have been wiped out from your hard drive if the ransom demand is not met.
That’s basically how the Jigsaw character in the horror series performs its criminal and brutal activity, giving its victims a short period of time to meet its demands or answer its questions, otherwise the victim will be killed in a cruel setup of deathly machines and gears.
Thankfully, the method developed by BleepingComputer experts provides an answer to this woe. First, launch the Windows Task Manager and remove the firefox.exe or drpbx.exe running processes, which are created by the Jigsaw malware to execute the encryption of files and lock out users from their computer.
After that, open the Windows MSConfig and by disabling the startup entry that leads to the firefox.exe process, you will be able to stop the ransomware from further deleting additional files.